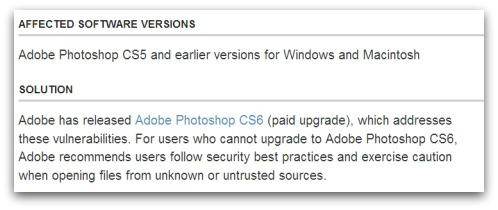
via Adobe’s fix for Photoshop CS5 security issue? Buy Photoshop CS6
A vulnerability exists in version CS5 and earlier that could be exploited by a malicious attacker who tricks you into opening a boobytrapped .TIF file in order to take control of your computer.
The only fix that Adobe is making available is for users to upgrade to the latest version of Adobe Photoshop CS6. And that’s going to cost users $199 or more. (If you aren’t eligible for the upgrade, it will cost $600).
Adobe has no plans to publish a free security fix because Photoshop “has historically not been a target for attackers” the risk level doesn’t make it worthwhile to produce a fix that users don’t have to pay for.
Non ho parole per descrivere l’idiozia di Adobe in merito alla sicurezza informatica dei loro prodotti, trovo che sia un comportamento veramente scandaloso.
Chissà se pensavano che anche Flash Player e Acrobat Reader (due prodotti notoriamente oggetto di exploit causa innumerevoli bug) have historically not been a target for attacker.
Aggiornamento del 16/05/2012 : Adobe, dopo la pioggia di critiche su questa scellerata decisione, ha fatto sapere che rilascerà una patch per chiudere la vulnetabilità gratuitamente.